Why is zero trust better?
Structure articles using HTML formatting without the HTML, head, body, and title tags.
Summary
Contents
- 1 Summary
- 2 Main Thought (Not a Question)
- 3 Main Thought (Not a Question)
- 4 Key Points
- 5 1. Main Thought (Not a Question)
- 6 2. Main Thought (Not a Question)
- 7 3. Main Thought (Not a Question)
- 8 4. Main Thought (Not a Question)
- 9 5. Main Thought (Not a Question)
- 10 6. Main Thought
- 11 7. Main Thought
- 12 8. Main Thought
- 13 9. Main Thought
- 14 10. Main Thought
- 15 11. Main Thought
- 16 Questions and Answers
Main Thought (Not a Question)
Main Thought (Not a Question)
Key Points
1. Main Thought (Not a Question)
2. Main Thought (Not a Question)
3. Main Thought (Not a Question)
4. Main Thought (Not a Question)
Some text of approximately 300 words (not a question).
5. Main Thought (Not a Question)
Some text of approximately 300 words.
6. Main Thought
Some text of approximately 300 words.
7. Main Thought
Some text of approximately 300 words.
8. Main Thought
Some text of approximately 300 words.
9. Main Thought
Some text of approximately 300 words.
10. Main Thought
Some text of approximately 300 words.
11. Main Thought
Some text of approximately 300 words.
Questions and Answers
1. Question1
2. Question2
3. Question3
Answer
4. Question4
Answer
5. Question5
Answer
6. Question6
Answer
7. Question7
Answer
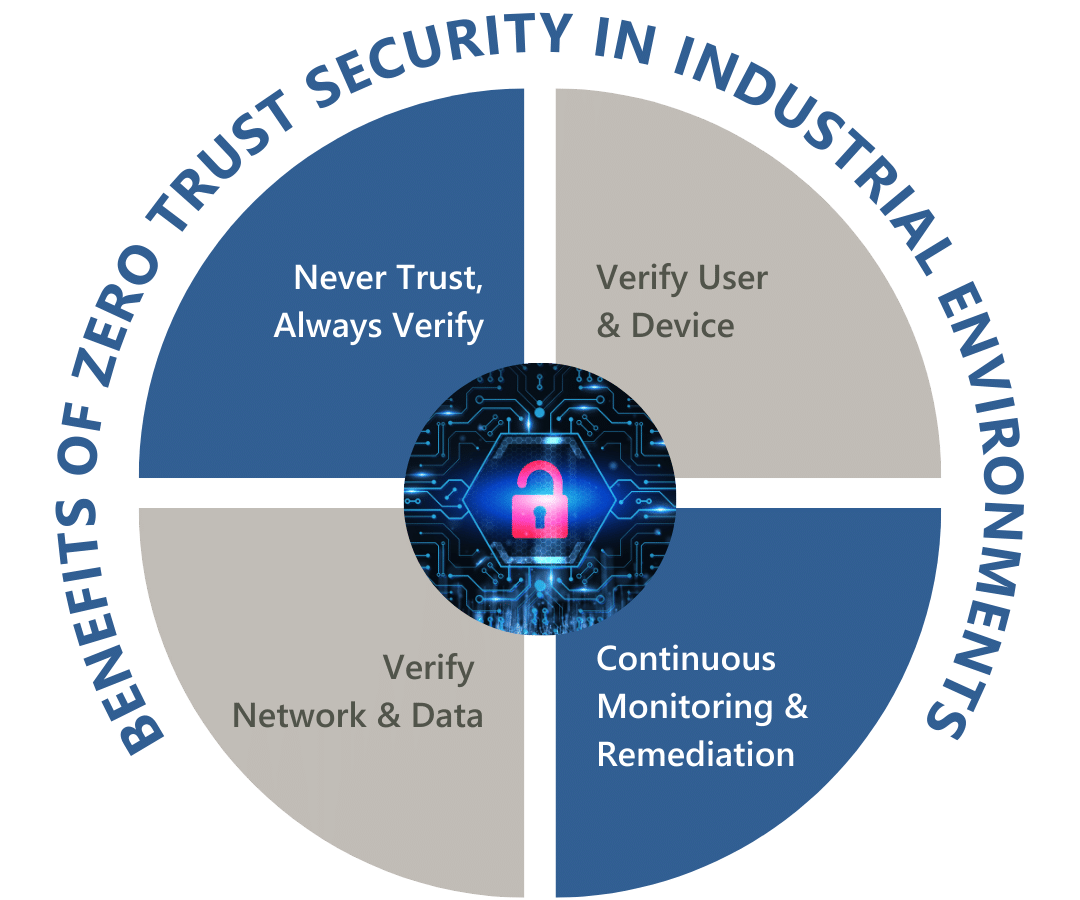
What are the pros and cons of zero trust?
The Pros and Cons of Zero Trust Security:
Cons: More applications, devices, and users to monitor.
Pros: Reduce susceptibility to insider attacks.
Cons: Zero Trust can take time security teams don’t have.
Pros: Discovering user identity and permissions.
Cons: Data, data, everywhere…
Pros: Narrowing the attack surface.
Why is zero trust policy important?
Zero-trust security policies allow organizations to define how user identities, device security posture, and fine-grained access control interact. They ensure that the principle of least privilege always applies, regardless of the device, location of the user, or location of the service they connect to.
What are the downsides of zero trust?
5. Zero Trust Can Be Costly. Another disadvantage of Zero Trust is that it can be costly to implement. This is because it requires more manpower and additional security measures — such as multi-factor authentication — which can add to the overall cost of the system.
How is zero trust better than VPN?
Instead of establishing a small perimeter within the network, zero trust protects the entire network’s security — and, more specifically, the information assets within it — by individually verifying each user and device before granting access to a given application.
What are the three main concepts of Zero Trust?
There are three key components in a zero trust network: user/application authentication, device authentication, and trust.
What are the three core principles of Zero Trust?
As business and technology continue to evolve, the three core principles of Zero Trust security remain consistent. Never trust. Always verify. Implement Zero Trust security for your business.
What are three potential benefits of adopting a zero trust strategy?
Benefits of implementing a Zero Trust Architecture:
– Offers threat protection against both internal and external threats.
– Provides increased visibility into all user access.
– Limits the possibility of data exfiltration.
– Secures Cloud adoption.
– Ensures data privacy.
– Enables hybrid workforce security.
What are the 4 goals of zero trust?
The strategy unveiled in the fall outlined four high-level goals for achieving the DOD’s vision for a zero trust architecture including cultural adoption, security and defense of DOD information systems, technology acceleration, and zero trust enablement.
What is the biggest challenge for zero trust?
Top 6 challenges of a zero-trust security model:
– A piecemeal approach to zero-trust cybersecurity can create gaps.
– All-in-one zero-trust products don’t exist.
– Legacy systems may not adapt to zero trust.
– Zero trust requires ongoing administration, maintenance.
– Zero trust can hinder productivity.
Why does zero trust fail?
However, the most prevalent obstacles in adopting Zero Trust were the lack of knowledge about the framework and the lack of buy-in from senior management. And the resounding result is that Gartner predicts that over 50% of organizations will fail to realize the benefits of Zero Trust.
Will zero trust replace VPN?
An SDP is a network architecture that implements zero-trust principles to provide more secure remote access than VPNs. Many experts predict VPNs will eventually become obsolete as zero trust and SDP adoption grows. For now, however, VPN use remains widespread.
Why a zero trust approach is key to cybersecurity now?
In the zero trust approach, security controls are deployed with the assumption that the network is already compromised. No unauthorized processes or applications are allowed to execute, and authentication is required for access to data.
What are the 4 goals of Zero Trust?
The strategy unveiled in the fall outlined four high-level goals for achieving the DOD’s vision for a zero trust architecture, including cultural adoption, security and defense of DOD information systems, technology acceleration, and zero trust enablement.

What are the pros and cons of zero trust
The Pros and Cons of Zero Trust SecurityCon: More applications, devices, and users to monitor.Pro: Reduce susceptibility to insider attacks.Con: Zero Trust can take time security teams don't have.Pro: Discovering user identity and permissions.Con: Data, data, everywhere…Pro: Narrowing the attack surface.
Why is zero trust policy important
Zero-trust security policies allow organizations to define how user identities, device security posture, and fine-grained access control interact. They ensure that the principle of least privilege always applies, regardless of the device, location of the user, or location of the service they connect to.
What are the downsides of zero trust
5. Zero Trust Can Be Costly. Another disadvantage of Zero Trust is that it can be costly to implement. This is because it requires more manpower and additional security measures — such as multi-factor authentication — which can add to the overall cost of the system.
How is zero trust better than VPN
Instead of establishing a small perimeter within the network, zero trust protects the entire network's security—and, more specifically, the information assets within it—by individually verifying each user and device before granting access to a given application.
What are the three main concepts of Zero Trust
There are three key components in a zero trust network: user/application authentication, device authentication, and trust.
What are the three core principles of Zero Trust
As business and technology continue to evolve, the three core principles of Zero Trust security remain consistent. Never trust. Always verify. Implement Zero Trust security for your business.
What are three potential benefits of adopting a zero trust strategy
Benefits of implementing a Zero Trust ArchitectureOffers threat protection against both internal and external threats.Provides increased visibility into all user access.Limits the possibility of data exfiltration.Secures Cloud adoption.Ensures data privacy.Enables hybrid workforce security.
What are the 4 goals of zero trust
The strategy unveiled in the fall outlined four high-level goals for achieving the DOD's vision for a zero trust architecture including cultural adoption, security and defense of DOD information systems, technology acceleration and zero trust enablement.
What is the biggest challenge for zero trust
Top 6 challenges of a zero-trust security modelA piecemeal approach to zero-trust cybersecurity can create gaps.All-in-one zero-trust products don't exist.Legacy systems may not adapt to zero trust.Zero trust requires ongoing administration, maintenance.Zero trust can hinder productivity.
Why does zero trust fail
However, the most prevalent obstacles in adopting Zero Trust were the lack of knowledge about the framework and the lack of buy-in from senior management. And the resounding result is that Gartner predicts that over 50% of organizations will fail to realize the benefits of Zero Trust.
Will zero trust replace VPN
An SDP is a network architecture that implements zero-trust principles to provide more secure remote access than VPNs. Many experts predict VPNs will eventually become obsolete as zero trust and SDP adoption grows. For now, however, VPN use remains widespread.
Why a zero trust approach is key to cyber security now
In the zero trust approach, security controls are deployed with the assumption that the network is already compromised. No unauthorized processes or applications are allowed to execute and authentication is required for access to data.
What are the 4 goals of Zero Trust
The strategy unveiled in the fall outlined four high-level goals for achieving the DOD's vision for a zero trust architecture including cultural adoption, security and defense of DOD information systems, technology acceleration and zero trust enablement.
What are the 5 pillars of Zero Trust
The five pillars of the Zero Trust Maturity Model are: Identity; Devices; Network, Data, and Applications and Workloads.
What are the 5 pillars of zero trust
The five pillars of the Zero Trust Maturity Model are: Identity; Devices; Network, Data, and Applications and Workloads.
What are the three core principles of zero trust
As business and technology continue to evolve, the three core principles of Zero Trust security remain consistent. Never trust. Always verify. Implement Zero Trust security for your business.
What are the three main concepts of zero trust
There are three key components in a zero trust network: user/application authentication, device authentication, and trust.
Why VPN is no longer secure
A VPN doesn't protect you from hackers
Hackers often use VPNs to gain access to networks. If your business has many third-party vendors, and each vendor has full access to your network, a hacker now has multiple potential routes to break into and exploit your network using VPN traffic.
Is there a better solution than VPN
The Onion Router
The Onion Router (Tor) network protects user data by encapsulating the data in multiple layers of secure encryption — using the Onion Protocol — as it routes the data from sender to receiver. The Tor process ensures that a user's identity is protected from ISPs and advertisers.
What are the 7 core pillars of Zero Trust
by DriveLockWHAT IS A ZERO TRUST MODELTHE ZERO-TRUST MODEL FOR MORE EFFECTIVE SECURITY IS BASED ON THE FOLLOWING PILLARS. 2.1 ZERO TRUST NETWORKS. 2.2 ZERO TRUST WORKLOADS. 2.3 ZERO TRUST DEVICES. 2.4 ZERO TRUST DATA. 2.5 ZERO TRUST PEOPLE.VISIBILITY AND ANALYTICS.AUTOMATION AND ORCHESTRATION.
Why companies are moving away from VPN
It matters because one compromised device can wreak havoc on your network and data. VPNs provide access not only to an intended resource but may also grant access to the entire company network. If this is the case, it is difficult to have visibility into who has access, and to what resources.
What kind of security loophole does VPN have
But VPNs have vulnerabilities
These VPN loopholes allow attackers to retrieve sensitive corporate data, including authentication credentials. Adversaries can use these stolen credentials to connect to the VPN and change configuration settings, or connect to other internal resources.
What technology will replace VPN
Two of the most common choices are software-defined WAN (SD-WAN) and Secure Access Service Edge (SASE). SD-WAN is designed to be a more efficient alternative to the VPN. Instead of implementing point-to-point connectivity, SD-WAN provides optimal routing of encrypted traffic between a network of SD-WAN appliances.
What will replace VPN
Secure alternatives to VPNs for remote workingZero trust network access.Secure access service edge (SASE)Software-defined perimeter.Software-defined wide area networks.Identity and access management and privileged access management.Unified endpoint management tools.
What are the two key capabilities of Zero Trust systems
Some of the core functions of a zero trust architecture include:Identify: An effective zero trust architecture requires in-depth knowledge of an enterprise's environment and how it is used.Protect: A zero trust strategy protects against cyber threats by managing access to corporate resources.