How does dVPN work?
Summary
Contents
- 1 Summary
- 2 Decentralized VPNs (dVPNs)
- 3 Key Points
- 4 1. How does a decentralized VPN work?
- 5 2. How does Sentinel dVPN work?
- 6 3. What are the disadvantages of decentralized VPNs?
- 7 4. Is a decentralized VPN good?
- 8 5. What is the difference between Tor and decentralized VPNs?
- 9 6. Does a VPN protect your crypto?
- 10 7. Is Sentinel dVPN safe?
- 11 8. Is Sentinel dVPN free?
- 12 9. What are the weaknesses of decentralized VPNs?
- 13 10. What is the difference between VPN and dVPN?
- 14 11. Should I use a VPN and Tor together?
- 15 12. Should I still use a VPN with Tor?
- 16 13. What does a VPN not protect against?
- 17 14. Should I use a VPN with Coinbase?
- 18 Conclusion
In this article, I will be discussing decentralized virtual private networks (dVPNs) and their key features. I will also address some common questions about dVPNs and compare them to traditional VPN systems. By the end, you will have a clear understanding of how dVPNs work and whether they are a suitable option for your online privacy and security.
Decentralized VPNs (dVPNs)
A decentralized VPN is a VPN service that does not have a single entity controlling its servers. Instead, it operates using a decentralized infrastructure, typically based on blockchain technology and smart contracts, with the help of other users who act as volunteers running nodes. This self-governing architecture ensures that there is no central authority controlling or monitoring the network.
Key Points
1. How does a decentralized VPN work?
A decentralized VPN operates using blockchain technology, smart contracts, and a network of user nodes. Instead of relying on a central server, the VPN service is distributed across these nodes, providing a more secure and private connection.
2. How does Sentinel dVPN work?
Sentinel dVPN is a blockchain-based decentralized VPN service that allows users to access a global network of community-managed servers. Its mobile and desktop apps provide a secure gateway to the internet, utilizing the power of the decentralized network.
3. What are the disadvantages of decentralized VPNs?
One potential disadvantage of decentralized VPNs is the limited network size and speed. The performance of the network depends on the number of active nodes and their resources, which can affect the overall speed and reliability of the VPN service.
4. Is a decentralized VPN good?
Decentralized VPNs offer the advantage of no centralized logs, ensuring greater privacy. However, there are concerns about the potential exploitation of users’ bandwidth by suspicious dVPN providers and the need for certain logging to protect against IP blacklisting.
5. What is the difference between Tor and decentralized VPNs?
Tor and decentralized VPNs serve similar purposes in providing online privacy and anonymity. However, the main difference lies in the underlying technology. Tor routes internet traffic through a network of volunteer-operated servers, while a decentralized VPN creates an encrypted tunnel between the user’s device and a remote server.
6. Does a VPN protect your crypto?
A VPN is designed to establish an encrypted and secure connection over a public network, making it valuable for protecting security and data privacy in the realm of cryptocurrencies and blockchain transactions.
7. Is Sentinel dVPN safe?
Sentinel dVPN is an interoperable and secure network layer offering various decentralized native services, including dVPN, dChat, and dVoIP. Its decentralized architecture ensures greater security and privacy.
8. Is Sentinel dVPN free?
Yes, Sentinel offers a decentralized VPN service that is available for free to users.
9. What are the weaknesses of decentralized VPNs?
Decentralized VPNs may face challenges in terms of policy coordination and the need for trained personnel to ensure smooth operations and maintenance of the network.
10. What is the difference between VPN and dVPN?
A decentralized VPN, or dVPN, differs from traditional VPNs in that it does not rely on a centralized control infrastructure. Instead, its servers are hosted and maintained by independent users, either using dedicated server machines or installing dVPN software on their home computers.
11. Should I use a VPN and Tor together?
Using a VPN and Tor together can provide maximum security and privacy as the VPN encrypts your entire traffic, while Tor provides anonymous routing through volunteer-operated servers.
12. Should I still use a VPN with Tor?
While not required, using a VPN with Tor offers added security and encryption, protecting your traffic from your Internet Service Provider (ISP). However, not all VPNs offer Tor features, so choosing a VPN with this capability is important.
13. What does a VPN not protect against?
A VPN provides encryption and IP masking, but it does not offer comprehensive protection like anti-virus software. It cannot prevent visits to phishing websites or the downloading of compromised files, for example.
14. Should I use a VPN with Coinbase?
If you want to bypass geo-restrictions or enhance your security while accessing Coinbase, using a VPN can be beneficial. It allows you to access Coinbase’s services even if they are not available in your country, ensuring privacy and security of your transactions.
Conclusion
Decentralized VPNs provide an alternative approach to traditional VPN services, offering greater privacy and control over your online activities. While they have certain limitations, such as network size and speed, they can be a suitable option for those who prioritize privacy and security. By understanding the key points and differences between decentralized VPNs and traditional VPNs, you can make an informed decision about whether dVPNs are the right choice for your needs.
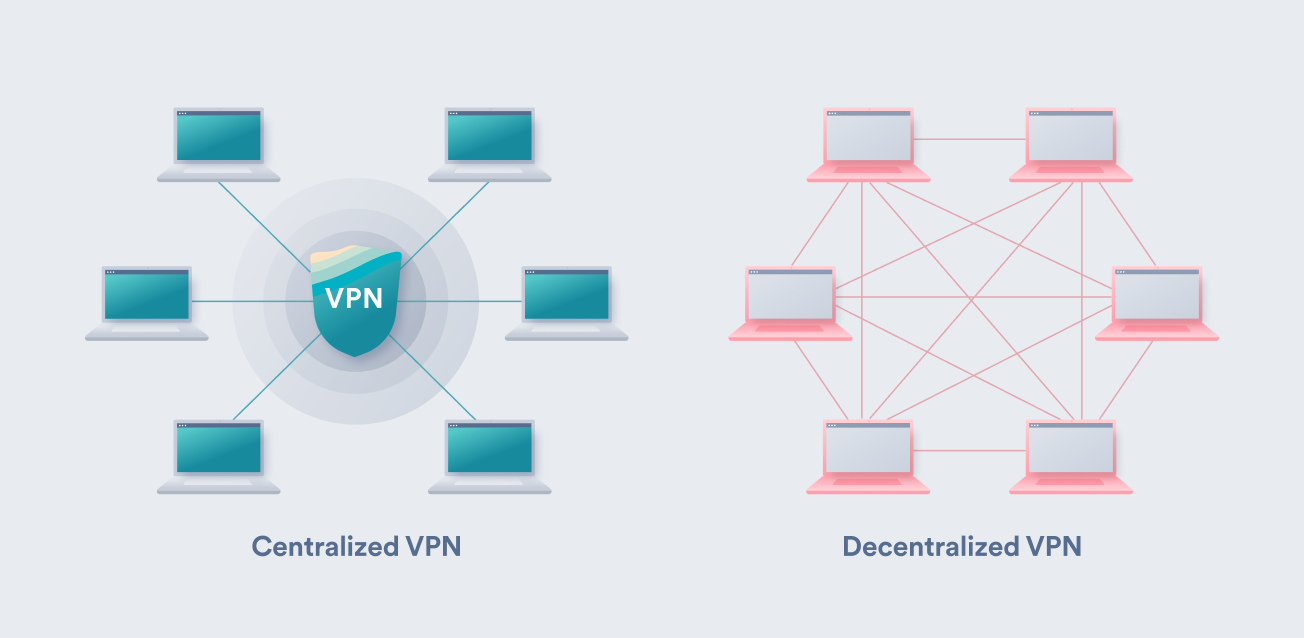
How does a decentralized VPN work
Decentralized VPNs or dVPNs represent VPN services that do not have a single entity controlling their servers. Instead, it operates with the help of blockchain, smart contracts, and other users. Ideally, such VPNs are mostly self-governing infrastructures consisting of volunteers that set up nodes.
Cached
How does Sentinel dVPN work
Independent and Autonomous Applications built on Sentinel
SOLAR dVPN is a blockchain-based decentralized VPN service. Using mobile & desktop apps, it allows you to access hundreds of community-managed servers all around the world and use them as your private & secure gateway to the Internet.
What are the disadvantages of decentralized VPN
Limited Network Size and Speed
As decentralized VPN devices rely on the computing power and bandwidth of network participants, the speed and performance of the network can be impacted by the number of active nodes and their resources.
Is a decentralized VPN good
While decentralized VPNs offer the benefit of no centralized logs, there are still certain concerns associated with the way they work. For instance, the potential exploitation of users' bandwidth by suspicious dVPN providers and the need for certain logging to protect against IP blacklisting.
Cached
What is the difference between Tor and decentralized VPN
Tor, short for “The Onion Router,” is a decentralized network that routes your internet traffic through a series of volunteer-operated servers, providing anonymity. A VPN, on the other hand, creates an encrypted tunnel between your device and a remote server, offering privacy and security.
Does a VPN protect your crypto
A VPN is designed to establish an encrypted and secure connection over a public network, usually the Internet. They are typically used to protect security and data privacy, making them a valuable tool in the realm of cryptocurrencies and blockchain.
Is Sentinel DVPN safe
Sentinel is an interoperable secure network layer offering the Sentinel Service Chain exclusively for distributed & decentralized native services like – dVPN, Sentrix (dChat and dVoIP) and more.
Is Sentinel DVPN free
Sentinel Decentralized VPN (Free)
What is the weakness of decentralized
There is a lack of uniformity in the policies followed. There will be a problem of coordination. It will require hiring of trained and qualified personnel.
What is the difference between VPN and dVPN
A decentralized VPN is a VPN that doesn't have centralized control of its servers. Instead of a single VPN provider supplying and maintaining the servers, dVPN's servers are hosted by independent users. They could be using dedicated server machines or just installing dVPN software on their home computers.
Should I use a VPN and Tor together
Yes! Using Tor and a VPN together provides maximum security.
Should I still use a VPN with Tor
A VPN isn't a requirement to use Tor, but it helps a lot. It encrypts your whole traffic, masking it from the ISP. In short, it's much safer to use Tor with a VPN. Not all VPNs offer Tor features in their product.
What does VPN not protect against
It's important to remember that VPNs do not work in the same way as comprehensive anti-virus software. While they will protect your IP and encrypt your internet history, but that is as much as they can do. They won't keep you safe, for instance, if you visit phishing websites or download compromised files.
Should I use a VPN with Coinbase
If you're wondering why one should use a VPN for Coinbase, the answer is quite simple. Here are the main reasons why Coinbase VPNs are useful: Bypass geo-restrictions. If you're located in a country where cryptocurrency conversion services are not available, you won't be able to access Coinbase unless you use a VPN.
What is the difference between VPN and DVPN
A decentralized VPN is a VPN that doesn't have centralized control of its servers. Instead of a single VPN provider supplying and maintaining the servers, dVPN's servers are hosted by independent users. They could be using dedicated server machines or just installing dVPN software on their home computers.
Which VPN is free for Ukraine location
ExpressVPN: Our Top Free VPN for Ukraine (for 30 Days)
The first premium provider we oughta talk about is ExpressVPN. Trust us – this is THE best free VPN for Ukraine, as it allows for a 30-day money-back policy. The entire solution actually revolves around this policy.
What are the major downsides of decentralized exchanges
Disadvantages of using DEXs. Despite the above advantages, there are various drawbacks of decentralized exchanges including a lack of technical knowledge needed to interact with these exchanges, the amount of smart contract vulnerabilities and unvetted token listings.
What are the three disadvantages of decentralization
Disadvantages of DecentralizationIssues with Coordination. Decentralization allows for the management of highly competent individuals to be carried out by highly skilled individuals.Factors from Outside.Increase the cost of administration.Operational costs are high.
What is the strongest VPN security protocol
Below are the main factors you should think of before choosing the right VPN for you: Security. OpenVPN and WireGuard are protocols that can offer the most robust encryption and the highest level of security.
Why would a criminal use a VPN
However, since VPNs are so good at ensuring privacy, they're often used by people who commit crimes such as downloading copyrighted media or planning ransomware attacks.
Does Tor hide you from your ISP
Tor Browser is anonymous in terms of hiding your location and browsing activity — but there are limits. Although they can't see your browsing activity or Tor encrypted data, your ISP can still see that you're using Tor.
How would the police track you if you use a virtual machine Tor and a VPN in one virtual machine
If the law enforcement can gain access to the end nodes, and intermediate nodes they can track you. If you use TOR, VPN, and virtual machine. It will be hard because it will require the law enforcement agency to intercept every TOR node, VPN provider and Virtual Machine provider on the route.
Why you shouldn’t use VPN all the time
Why shouldn't I use a VPN A VPN might reduce your connection speed even if your internet service provider isn't throttling your speed; Using a VPN on mobile will increase your mobile data usage; Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
Can the police track a VPN
With a VPN on, the user's online activities and data are encrypted. But, if the VPN software has security flaws and vulnerabilities, the police (or any other third party, for that matter) can use them to “break into” the VPN and see what data is being sent and received. So technically, the policy could track a VPN.
Is using a VPN to trade crypto illegal
The legality of using a VPN with Binance or any other cryptocurrency exchange depends on the specific laws and regulations of your jurisdiction. In some countries, using a VPN to access restricted websites or services is legal, while in others it may be illegal or restricted.